PER Security Profiles
Description:
Security profiles and operating units that they give access to.
Parameters
Security Profile
Used tables
hr_all_organization_units_vl, per_security_profiles, per_organization_list, hr_operating_units, hr_locations_all, fnd_territories_vl
Categories
Related reports
Dependencies
If you would like to try one of these Oracle EBS SQLs without having Blitz Report installed, note that some of the reports require functions from utility package xxen_util.
Example Report
Report SQL
www.enginatics.com/reports/per-security-profiles/
Blitz Report™ import options
Case Study & Technical Analysis: PER Security Profiles Report
Executive Summary
The PER Security Profiles report is a crucial HR security and audit tool within Oracle E-Business Suite. It provides a comprehensive listing of all defined security profiles and, critically, details which operating units and organizations these profiles grant access to. This report is indispensable for HR system administrators, security officers, and auditors to manage and verify access to employee records, ensure compliance with data privacy regulations, and maintain a robust and auditable HR security framework.
Business Challenge
Controlling who can view and manage employee data is a fundamental requirement for HR and a major challenge in a complex ERP environment. Organizations often struggle with:
- Granular Access Control: Oracle HR allows for highly granular security down to individual employees, but understanding the cumulative effect of these settings is complex.
- Ensuring Data Privacy: Compliance with data privacy laws (e.g., GDPR, CCPA) requires clear visibility into what employee data users can access. Misconfigured security can lead to unauthorized data exposure.
- Auditing Security Settings: Regularly auditing HR security profiles to ensure they align with job roles and responsibilities is a critical but often manual and complex task.
- Troubleshooting Access Issues: When users report that they cannot see certain employees or organizations, diagnosing the underlying security profile configuration is a key troubleshooting step. A consolidated report accelerates this process.
The Solution
This report offers a clear, consolidated, and auditable view of security profile configurations, transforming how HR manages and verifies data access.
- Centralized Security Overview: It presents a detailed list of all security profiles, showing precisely which operating units and organizations each profile allows access to. This provides a holistic understanding of the data access landscape.
- Enhanced Compliance Audits: Security officers can use this report to quickly verify that security profiles are correctly configured, ensuring that sensitive employee data is protected and access is aligned with regulatory requirements and internal policies.
- Streamlined Access Review: The report facilitates regular reviews of HR security, allowing administrators to identify and rectify any inappropriate or excessive data access, thereby mitigating security risks and improving data governance.
- Accelerated Troubleshooting: When an HR user encounters access issues, this report provides immediate insight into the security profile assigned to their responsibility, helping to quickly pinpoint and resolve the problem.
Technical Architecture (High Level)
The report queries Oracle HR’s security definition tables and links them to the organizational structure.
- Primary Tables Involved:
per_security_profiles(the central table defining each security profile).per_organization_list(a table that often stores the organizations included in a security profile).hr_operating_units(for details of the operating units).hr_all_organization_units_vl(for the names and details of organizations).
- Logical Relationships: The report selects all security profiles from
per_security_profiles. It then determines the operating units and organizations that each profile grants access to, typically by queryingper_organization_listor by analyzing the security profile’s definition, and then joins tohr_all_organization_units_vlto display the user-friendly names of these organizations.
Parameters & Filtering
The report includes a straightforward parameter for targeted analysis of security profiles:
- Security Profile: Allows users to select a specific security profile to view its detailed access configuration. This is particularly useful when investigating a single profile or preparing for changes.
Performance & Optimization
As a report focused on setup data, it is designed for rapid performance.
- Low Data Volume: The underlying security profile and organizational definition tables contain a manageable number of rows, ensuring the query executes quickly.
- Indexed Joins: The queries leverage standard Oracle indexes on
security_profile_idandorganization_idfor efficient joins between the security and organizational tables.
FAQ
1. What is a ‘Security Profile’ in Oracle HR? A Security Profile is a mechanism in Oracle HR that defines the population of employees or organizations that a user can access. When a security profile is assigned to a responsibility, any user logging in with that responsibility will only be able to view and process data for the employees or organizations included in that profile.
2. How does this report help with managing data access for different HR roles? Different HR roles (e.g., Payroll Administrator, Benefits Specialist, HR Generalist) require different levels of access. This report helps HR system administrators design and audit security profiles for each role, ensuring that users only see the data relevant to their job functions.
3. Can this report also show which users are assigned to each security profile?
This report primarily focuses on the definition of the security profile itself (what data it grants access to). To see which users are assigned to each security profile, you would typically need a separate report that queries fnd_user and fnd_responsibility_vl and then links to the security profile assignments.
Oracle E-Business Suite Reporting Library
We provide an open source Oracle EBS SQLs as a part of operational and project implementation support toolkits for rapid Excel reports generation.
Blitz Report™ is based on Oracle EBS forms technology, and hence requires minimal training. There are no data or performance limitations since the output files are created directly from the database without going through intermediate file formats such as XML.
Blitz Report can be used as BI Publisher and Oracle Discoverer replacement tool. Standard Oracle BI Publisher and Discoverer reports can also be imported into Blitz Report for immediate output to Excel. Typically, reports can be created and version tracked within hours instead of days. The concurrent request output automatically opens upon completion without the need for re-formatting.
The Filters, Columns, Rows and Values fields are used to create and deliver the data in pivot table format with full drill down to details.
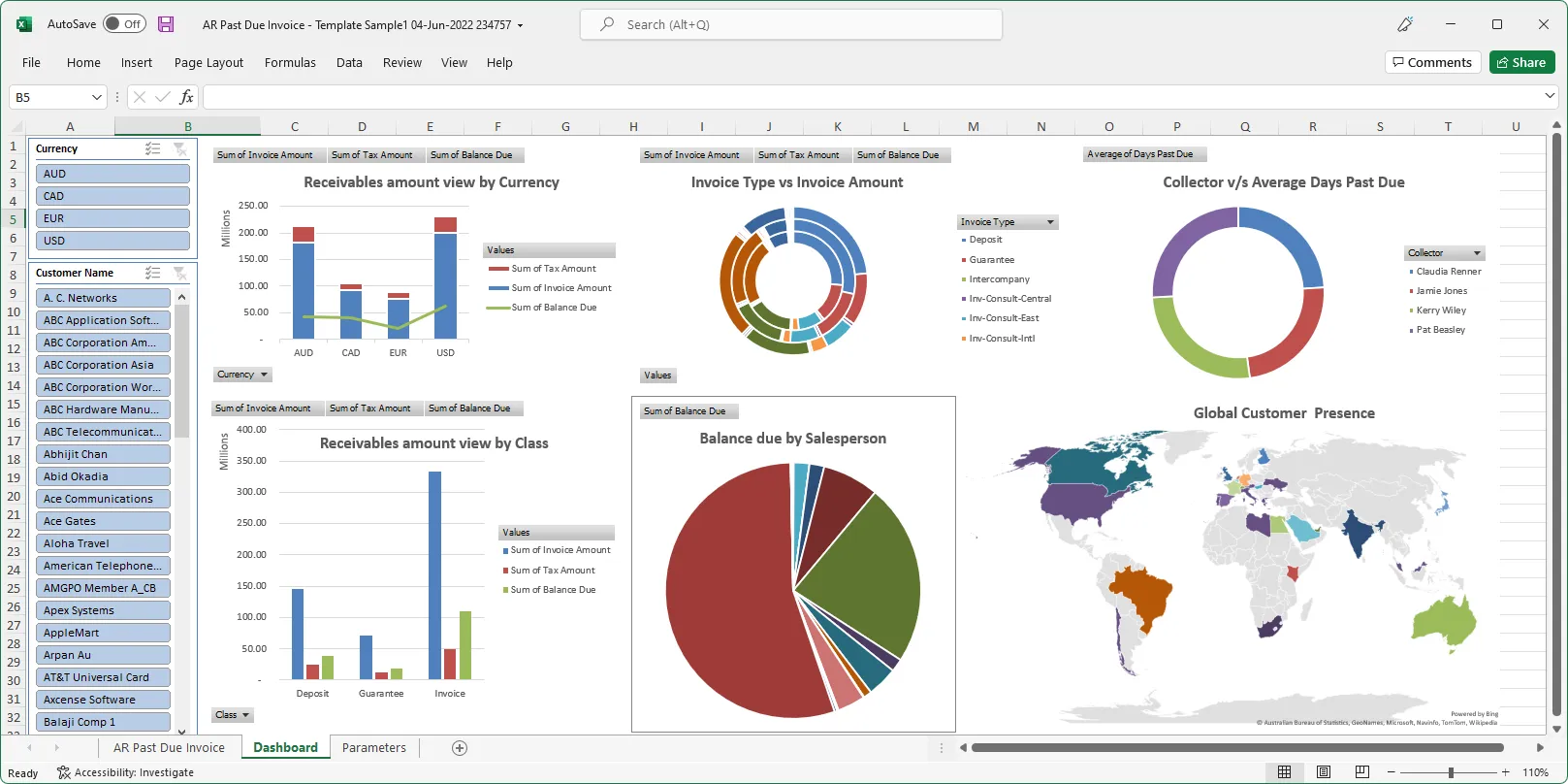
The Excel template upload functionality in Blitz Report allows users to create their own layouts by uploading an Excel template with additional sheets and charts, automatically refreshed when the report runs again. This allows to create custom dashboards and more advanced visualizations of report data.
You can download and use Blitz Report free of charge for your first 30 reports.
The installation and implementation process usually takes less than 1 hour; you can refer to our installation and user guides for specific details.
If you would like to optimize your Oracle EBS implementation and or operational reporting you can visit www.enginatics.com to review great ideas and example usage in blog. Or why not try for yourself in our demo environment.
Useful Links
Blitz Report™ – World’s fastest data upload and reporting for Oracle EBS
Oracle Discoverer replacement – importing worksheets into Blitz Report™
Blitz Report™ Questions & Answers
Supply Chain Hub by Blitz Report™
© 2025 Enginatics